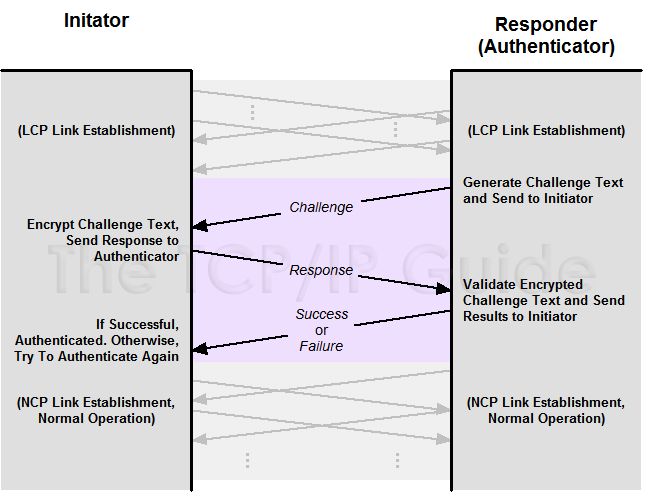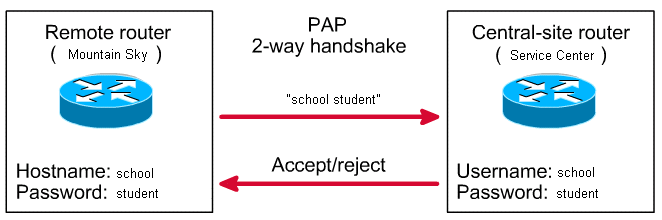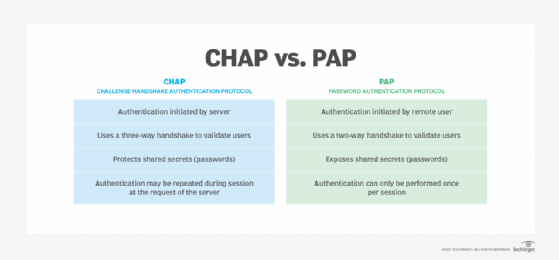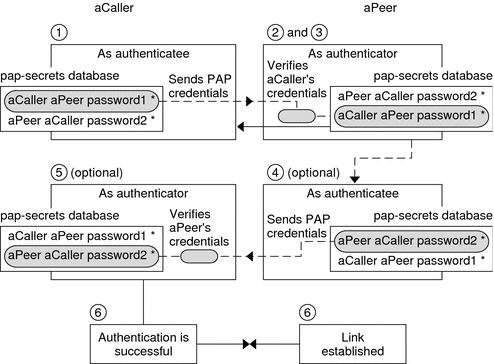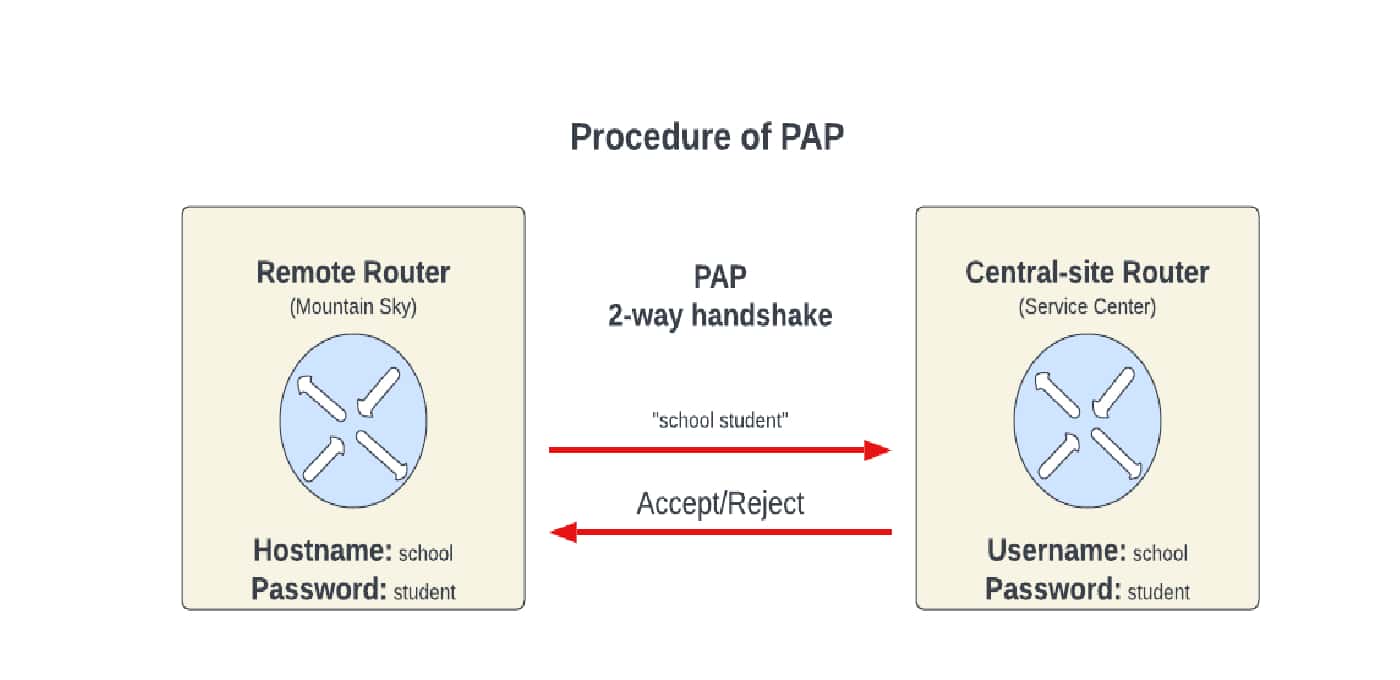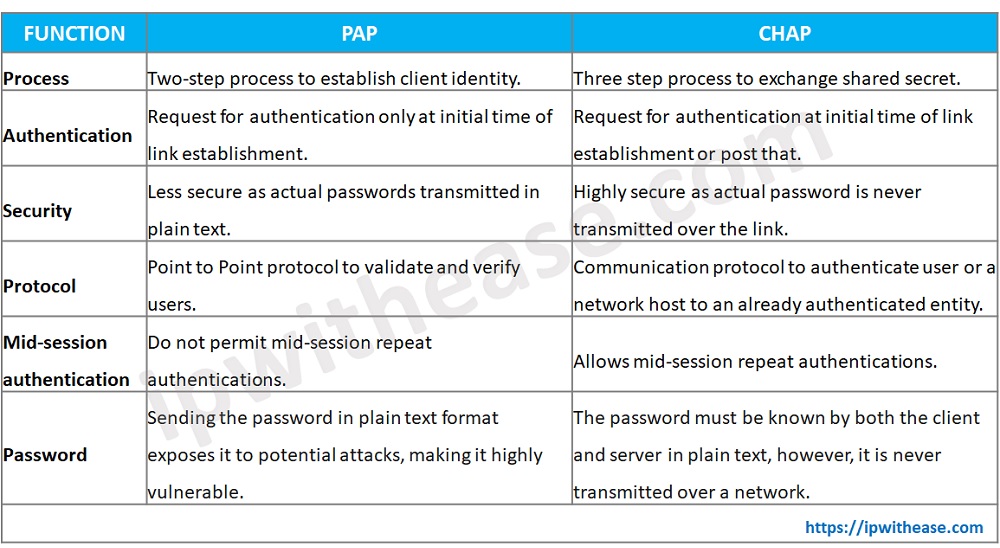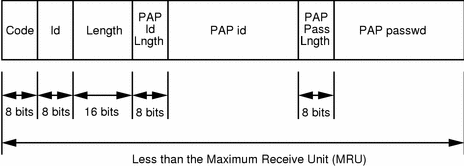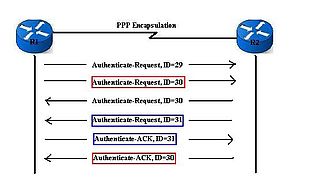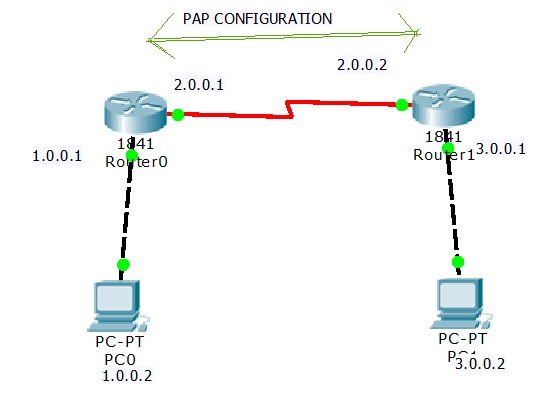
PAP(Password Authentical Protocol) Configuration on cisco router – Learn Linux CCNA CCNP CEH CISSP CISA Penetration-Testing Bug Bounty IPv6 Cyber-Security Network-Security Online
GitHub - Lithium876/PAP-POC: A proof of concept of how PAP (Password Authentication Protocol) works when authenticating users. This POC focuses on the fact that this protocol sends passwords our the network in

Pap Password Authentication Protocol Acronym Stock Illustration - Download Image Now - Acronym, Business, Computer - iStock

Pap Password Authentication Protocol Acronym Business Stock Vector (Royalty Free) 2018592065 | Shutterstock